SSH with Ubuntu 12.10 and nexus 7 as a client
I woke up one day and decided to view my logs, and I see someone poking hard at my ssh connection, trying to connect with a bunch of bogus usernames and passwords. Here are few tips to fend up the most basic of the attacks.
sudo vi /etc/hosts.deny </p>
# /etc/hosts.deny: list of hosts that are _not_ allowed to access the system.
# See the manual pages hosts_access(5) and hosts_options(5).
#
# Example: ALL: some.host.name, .some.domain
# ALL EXCEPT in.fingerd: other.host.name, .other.domain
#
# If you're going to protect the portmapper use the name "portmap" for the
# daemon name. Remember that you can only use the keyword "ALL" and IP
# addresses (NOT host or domain names) for the portmapper, as well as for
# rpc.mountd (the NFS mount daemon). See portmap(8) and rpc.mountd(8)
# for further information.
#
# The PARANOID wildcard matches any host whose name does not match its
# address.
#
# You may wish to enable this to ensure any programs that don't
# validate looked up hostnames still leave understandable logs. In past
# versions of Debian this has been the default.
# ALL: PARANOID
# rpcbind mountd nfsd statd lockd rquotad : ALL
ALL: ALLALL: 60.169.22.118in.telnetd: ALL
sudo vi /etc/hosts.allow </p>
# /etc/hosts.allow: list of hosts that are allowed to access the system.
# See the manual pages hosts_access(5) and hosts_options(5).
#
# Example: ALL: LOCAL @some_netgroup
# ALL: .foobar.edu EXCEPT terminalserver.foobar.edu
#
# If you're going to protect the portmapper use the name "portmap" for the
# daemon name. Remember that you can only use the keyword "ALL" and IP
# addresses (NOT host or domain names) for the portmapper, as well as for
# rpc.mountd (the NFS mount daemon). See portmap(8) and rpc.mountd(8)
# for further information.
#
# rpcbind mountd nfsd statd lockd rquotad : list of IP addresses
openvpn sshd: 192.168.12.0/255.255.255.248 10.85.0.0/255.255.255.252
ON THE SERVER
on the server edit /etc/ssh/sshd_config make sure you can access ssh with Password
PasswordAuthentication yes
We will disallow users to ssh with a password later, but this needs to be enabled so you can copy ssh keys to the host you tying to connect to.
ON THE CLIENT
Create a public and private SSH key on the command-line, increase number of bits to 4096, for added security protect with a password
mkdir ~/.ssh
chmod 700 ~/.ssh
cd ~/.ssh
ssh-keygen -t rsa -b 4096
ON THE NEXUS
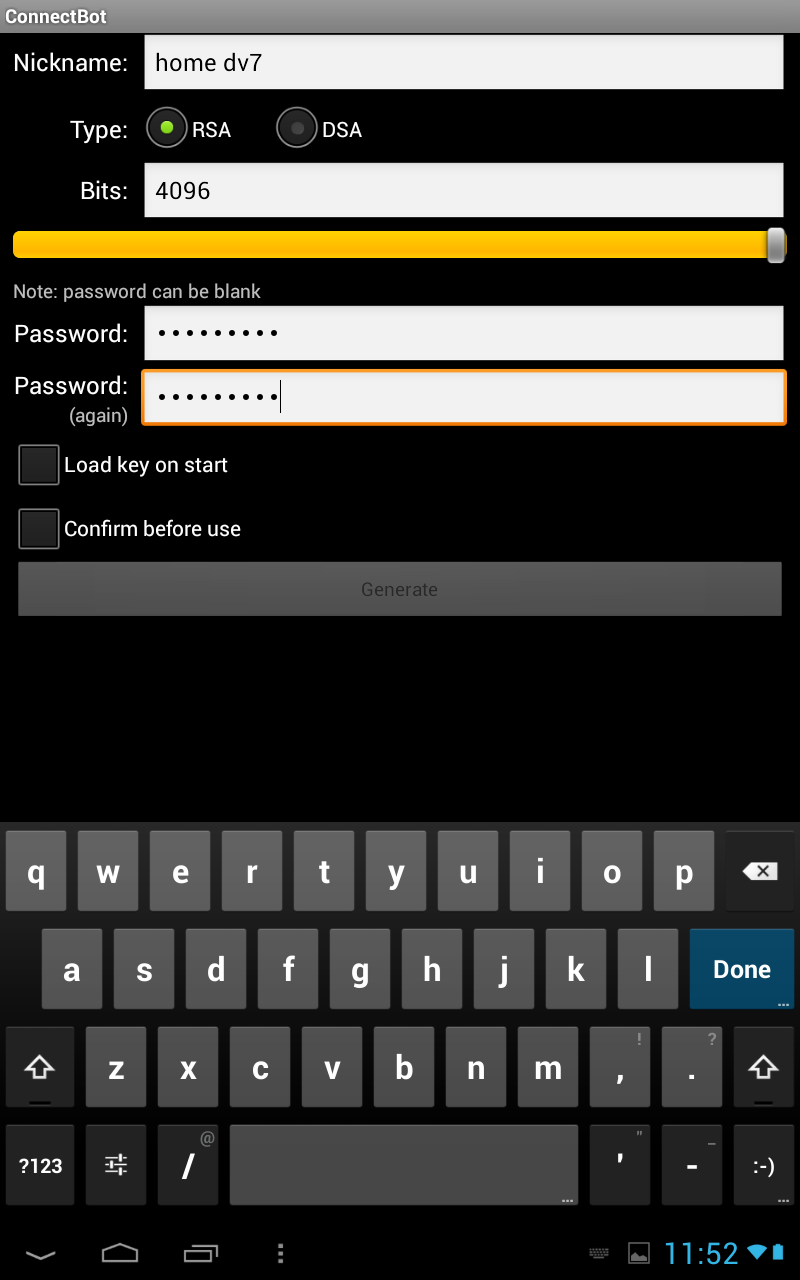
Download this app from the play store. I won't walk you through every screen, there were too many of them .
Click Menu > Manage Pubkeys > Generate
Use 4096 bit, and a password
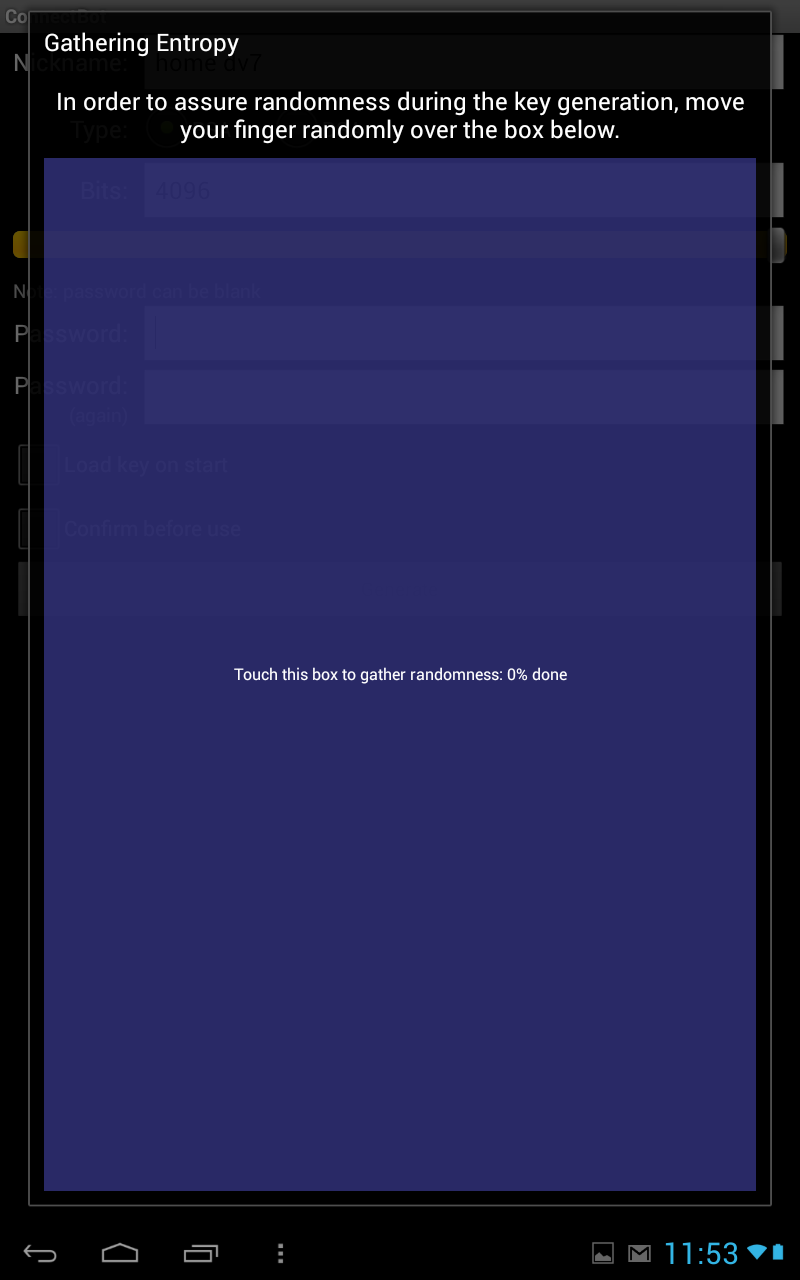
this is the fun part, randomly touch screen to generate an entropy
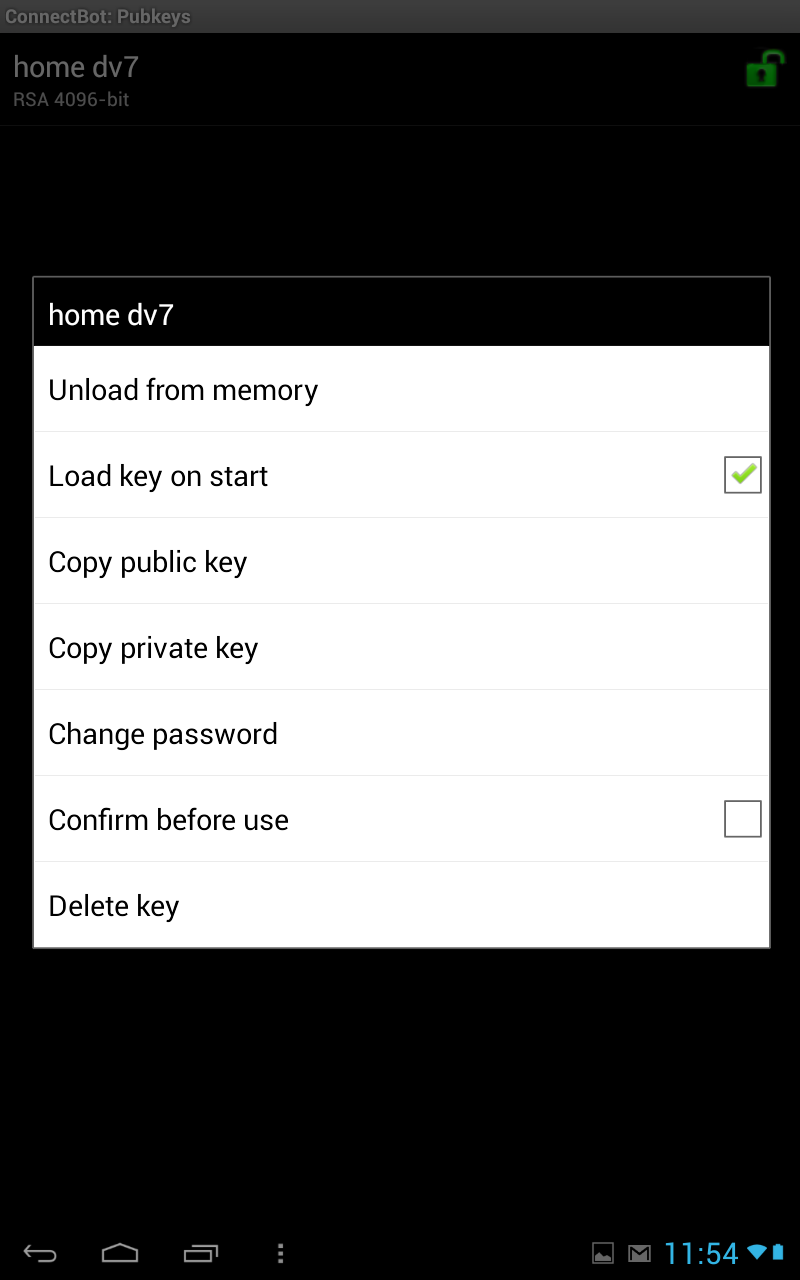
Once that is done, long press key, and check key on start. and long press copy public key
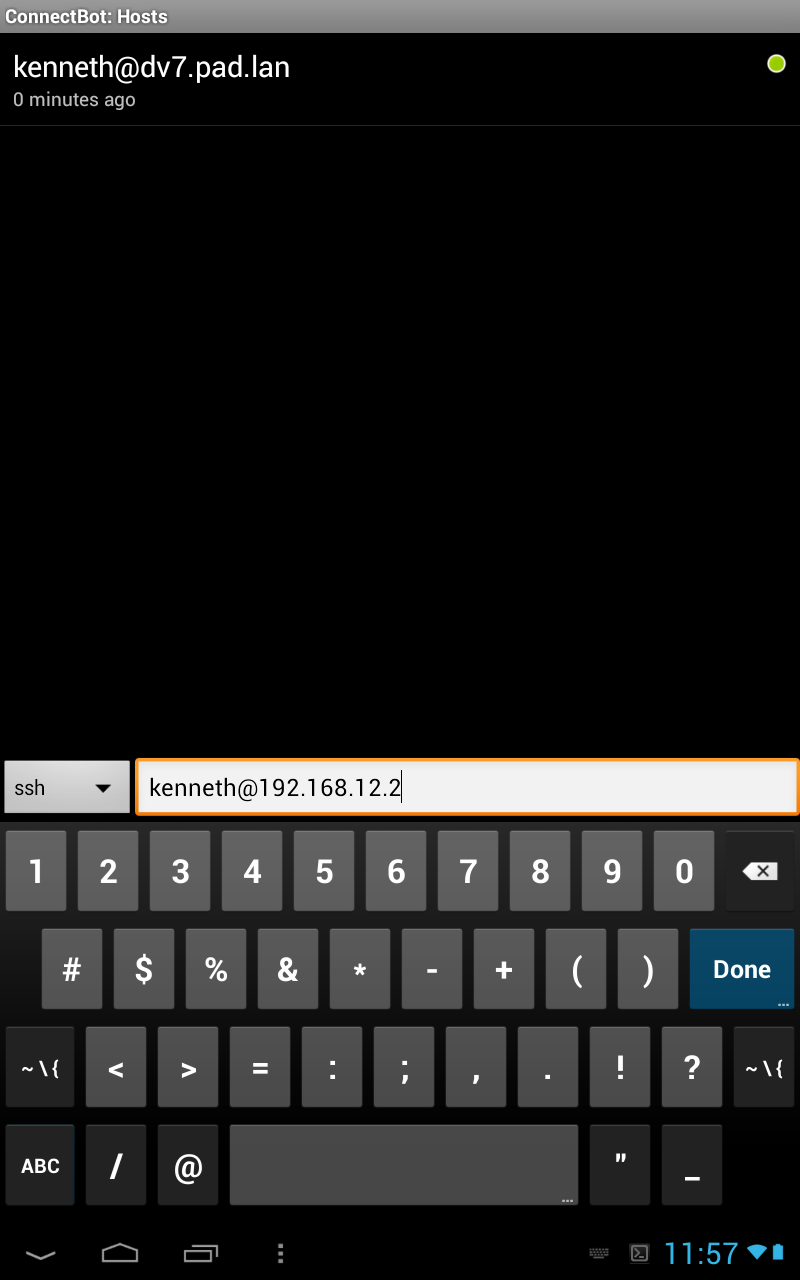
Go back to the main screen and create an ssh session, I have a dns server, but if you don't you might want to enter the ip of the host
Before you connect, long press, and edit host you should load keys, it should say, Use pubkey, and you select the one you just created.
It will fail with the key, because you haven't copied it over just yet. you'll have to enter the password, when you get here, do
echo "press menu and paste, your key should paste here" >> .ssh/authorized_keys
ON THE CLIENT
ssh-copy-id -i .ssh/id_rsa.pub kenneth@192.168.12.2</div>
ON THE SERVER
Now edit /etc/ssh/sshd_config, watch the highlighted values
# Package generated configuration file
# See the sshd_config(5) manpage for details
# What ports, IPs and protocols we listen for
Port 5848 #use a non standard port# Use these options to restrict which interfaces/protocols sshd will bind to
#ListenAddress ::
#ListenAddress 0.0.0.0
Protocol 2 #use protocol 2 more secure# HostKeys for protocol version 2
HostKey /etc/ssh/ssh_host_rsa_key
HostKey /etc/ssh/ssh_host_dsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
#Privilege Separation is turned on for security
UsePrivilegeSeparation yes
# Lifetime and size of ephemeral version 1 server key
KeyRegenerationInterval 3600ServerKeyBits 4096AllowUsers kenneth #specify what user can connect# Logging
SyslogFacility AUTH
LogLevel VERBOSE #log everything # Authentication:
LoginGraceTime 20 #tighten this time PermitRootLogin no #NEVER LET ROOT INStrictModes yesRSAAuthentication yesPubkeyAuthentication yes#AuthorizedKeysFile %h/.ssh/authorized_keys
# Don't read the user's ~/.rhosts and ~/.shosts files
IgnoreRhosts yes# For this to work you will also need host keys in /etc/ssh_known_hosts
RhostsRSAAuthentication no
# similar for protocol version 2
HostbasedAuthentication no# Uncomment if you don't trust ~/.ssh/known_hosts for RhostsRSAAuthentication
#IgnoreUserKnownHosts yes
# To enable empty passwords, change to yes (NOT RECOMMENDED)
PermitEmptyPasswords no# Change to yes to enable challenge-response passwords (beware issues with
# some PAM modules and threads)
ChallengeResponseAuthentication no# Change to no to disable tunnelled clear text passwords
PasswordAuthentication no# Kerberos options
#KerberosAuthentication no
#KerberosGetAFSToken no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
# GSSAPI options
#GSSAPIAuthentication no
#GSSAPICleanupCredentials yes
X11Forwarding no #x11vnc different certsX11DisplayOffset 10
PrintMotd no
PrintLastLog yes
TCPKeepAlive yes
#UseLogin no
#MaxStartups 10:30:60
Banner /etc/issue.net# Allow client to pass locale environment variables
AcceptEnv LANG LC_*
Subsystem sftp /usr/lib/openssh/sftp-server
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
UsePAM yes</p>
sudo vi /etc/issue
Makes it look like some FBI type warning when you login, you can get fancy here.
***************************************************************************
NOTICE TO USERS
This computer system is the private property of its owner, whether
individual, corporate or government. It is for authorized use only.
Users (authorized or unauthorized) have no explicit or implicit
expectation of privacy.
Any or all uses of this system and all files on this system may be
intercepted, monitored, recorded, copied, audited, inspected, and
disclosed to your employer, to authorized site, government, and law
enforcement personnel, as well as authorized officials of government
agencies, both domestic and foreign.
By using this system, the user consents to such interception, monitoring,
recording, copying, auditing, inspection, and disclosure at the
discretion of such personnel or officials. Unauthorized or improper use
of this system may result in civil and criminal penalties and
administrative or disciplinary action, as appropriate. By continuing to
use this system you indicate your awareness of and consent to these terms
and conditions of use. LOG OFF IMMEDIATELY if you do not agree to the
conditions stated in this warning.
****************************************************************************
sudo service ssh restart
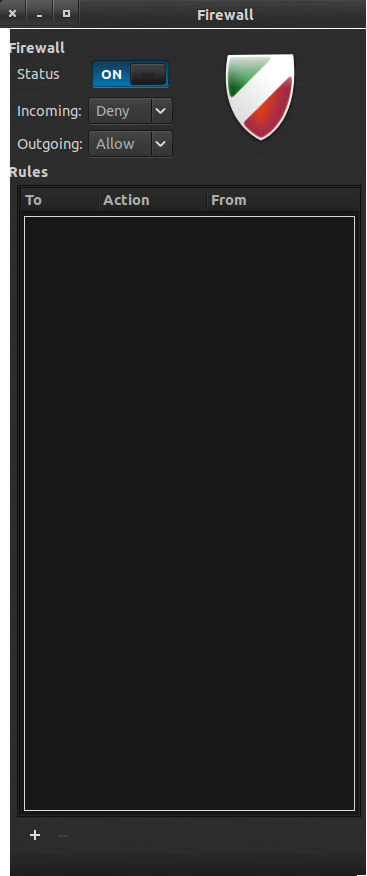
okay now we need to take care of the ports, and really I could take you through a very complicated session of iptables, but if you are interested, read on "PORT KNOCKING" and "LIMIT RATES"</p>
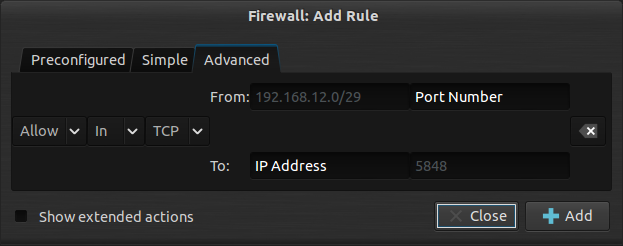
for the simplicity of my guid, i'll use gufw.
Click on edit, and add a rule, from specific subnet to the specific port, you can be as specific as to what ip, to, or what port number its emitting from. usually you don't specify what port from, clients like nexus, might be using ports not recognized by server. also add subnet for vpn.
sudo reboot now!
ssh -v -p 5848 kenneth@192.168.12.2
this is a config file so that you can type ssh dv7 and get straight in.
Host dv7
HostName 192.168.12.2
Port 5848
User kenneth
this simple command should get you
ssh dv7
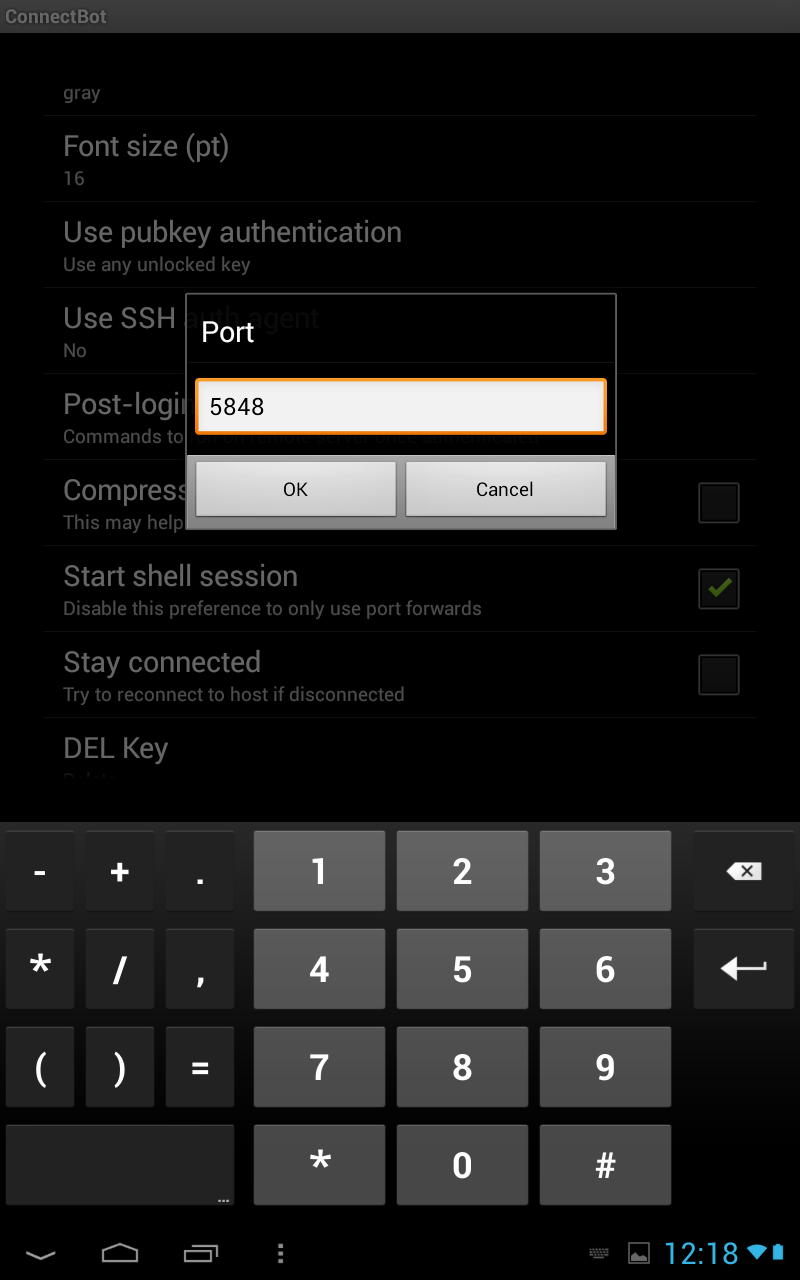
ON THE NEXUS
long press the connection you have created and edit the port.
you should now be able to get in directly
</div>People think it's absolutely unnecessary to have a password to a key pem, while you still connecting through vpn. I was hunting for the most secure way, so this is it.
*thnx to carl for the email to fix post formatting
to delete the key, you can use the following command
oh and the android keyboard sucks, get the hacker's keyboardcd ~/.ssh sed '/dv7$/d' authorized_keys | tee authorized_keys